API Key¶
Usage¶
Client MUST set Private-Token HTTP Request header and set it with proper Key in order to get access to protected API
Example:
curl -s -D - -k -H 'Private-Token: 12345' https://noc_url/datastream-api-referencemanagedobject`
where 12345 is an API token key.
Roles¶
DataStream API¶
Access to DataStream API
| API:Role | Description |
|---|---|
datastream:administrativedomain | administrativedomain DataStream |
datastream:alarm | administrativedomain DataStream |
datastream:resourcegroup | resourcegroup DataStream |
datastream:managedobject | managedobject DataStream |
datastream:dnszone | dnszone DataStream access |
datastream:cfgmetrics | cfgmetrics DataStream access |
datastream:cfgping | cfgping DataStream access |
datastream:cfgsyslog | cfgsyslog DataStream access |
datastream:cfgtrap | cfgtrap DataStream access |
datastream:vrf | vrf DataStream access |
datastream:prefix | prefix DataStream access |
datastream:address | address DataStream access |
NBI API¶
| API:Role | Description |
|---|---|
nbi:config | NBI config API access |
nbi:configrevisions | NBI configrevisions API access |
nbi:getmappings | NBI getmappings API access |
nbi:objectmetrics | NBI objectmetrics API access |
nbi:objectstatus | NBI objectstatus API access |
nbi:path | NBI path API access |
nbi:telemetry | NBI telemetry API access |
Web interface example¶
You should fill Name and API key as required fields. Also in API rows should be nbi or datastream. In Role row should be a role from tables above or * (asterisk)
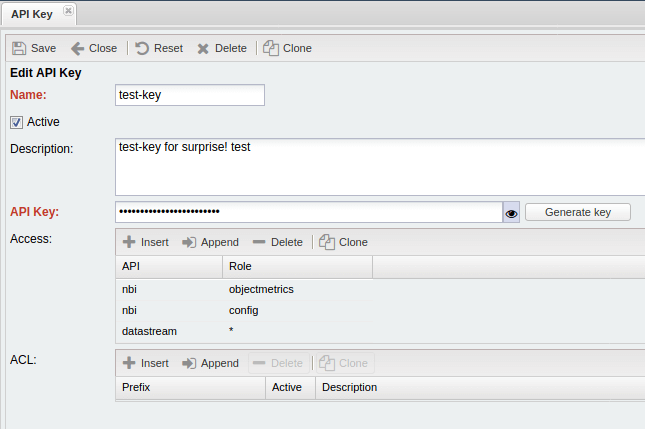
You can fill the ACL section or may leave it empty. Prefix field should be in a IP/net way.
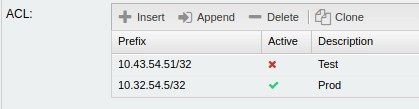
Also there is an opportunity to allow requests to API only from whitelist IPs. You can find this option in Tower, in nbi/datastream service respectively.
Best Practices¶
- Grant separate API Keys for every connected system
- Grant separate API Keys for every developer, Restrict key lifetime
- Grant separate API Keys for every external tester, Restrict key to short lifetime